& Construction

Integrated BIM tools, including Revit, AutoCAD, and Civil 3D
& Manufacturing

Professional CAD/CAM tools built on Inventor and AutoCAD
11 min read
Got a smartphone? Then chances are you’ve been living in a biometric world for years now. This type of technology is no longer reserved for your favorite spy movies, and you’re bound to find biometric technologies being used in all areas of your life, seen and unseen.
Biometrics are finally bringing us out of the age of having to remember a million different passwords, offering a new level of convenience and efficiency. And how does it do it? With you!
In the age of biometrics, you are the password. Does this maybe freak you out a bit, or are you excited for the end of password fatigue? Whichever way you spin it, the world of biometrics is here, and it’s all about you.
So what are biometrics? Simply put, it’s a technology that uses your unique qualities, like your fingerprints or facial features, to identify, well, you! By using your unique biological characteristics, you can provide measurements that are ideally suited for identification and authentication in a variety of applications and situations. There are a ton of methods to measure and identify yourself through biometrics, including:

Are we ready for biometrics? From iris to fingerprint scanning, the uses are everywhere! (Image source)
There are biometrics technologies that are based on your unique scent, voice, facial features, and even your veins. Some of these biometric identifiers you already use every day, like in your smartphone. You probably quickly fell in love with the ability to unlock your phone using only your fingerprint, right? Or maybe you enjoy the convenience of not having to whip out your wallet anymore to make a purchase? This and more all happens thanks to the world of biometrics, but how does it work?
At the heart of every biometric technology, whether that’s a fingerprint scanner or facial recognition, are three primary processes hard at work:
Enrollment
First, biometric recognition doesn’t just work with dark magic. You need to allow it to collect information from you through the use biometric hardware. This can be anything from scanning your fingertip to your iris. In this step, a biometric system is concerned solely with recording a unique piece of information about you.
Storage
Once a biometric system captures a piece of information about you, it then has to store it. Most systems won’t save something like your complete fingerprint, and will instead translate the physical ridges and valleys of your fingertips into points on a graph, which can then be translated into digital storage. This digital representation of your fingerprint is called a template.
Comparison
Now that your data has been enrolled and stored, it’s time to put it to use for some added convenience and efficiency. The next time you use a biometric system, it will compare a trait that you present to it, like your fingerprint, and use its existing data about your fingerprint to verify that you are in fact you. And if not, then it’s access denied!
The actual hardware being used in every biometric system is also largely the same. You’ll have a sensor that captures your data, which gets sent to a computer running software that makes the actual comparisons of data with some advanced algorithms. Pretty straightforward, right? Let’s take a look at the variety of biometric systems out there.
For those you spy movie lovers out there, you’ll feel right at home with iris scanning. This biometric technology is simpler than you might think, despite how futuristic it looks in movies. With an iris scanning system, you’ve got a basic charge-coupled device (CCD) camera, which makes use of both visible and near-infrared light to capture a high-contrast picture of your eye.

Iris scanning isn’t just for spy movies, and it’s a very simple biometric technology in use today. (Image source)
This type of high-contrast digital picture taking makes it easy to isolate your pupil from your iris, and allows computer software to determine several unique measurements, including the location of the center of your pupil, the edge of your pupil, the edge of your iris, and the location of your eyelids and eyelashes. All of these measurements unique to you can then be stored and referenced in future iris scans.
Just like irises or fingertips, veins are all 100% unique from individual to individual. And even better, most of your veins aren’t visible beneath your skin, so they’re also tampering proof!

We’ve all got a unique web of veins, ready for use in biometric applications. (Image source)
In vein biometrics, another charge-coupled device (CCD) camera is used, just like in iris scanning, which takes a digital picture with the help of some near-infrared light. The hemoglobin in your red blood cells, which carry oxygen, absorb this light, returning an image that shows your veins as black in a digital picture. And just like in iris scanning, an algorithm identifies the unique patterns in your veins, stores it, and uses it for future comparisons.
Where biometric technologies start to get advanced is what we’ve seen in smartphones these past few years. Many iPhone and Android phones ship with a built-in fingerprint scanner, allowing you to access all of your apps and even make payments with a simple scan of your finger. This technology has steadily evolved throughout the years, progressing from optical scanners to today’s capacitive scanners and the future’s ultrasonic scanners. Here’s how each one works:

The introduction of the Touch ID technology in the iPhone 5S introduced a new way to work with our smartphones. (Image source)
Optical Scanners
This is the first and oldest method of capturing data from fingerprints and relies on the old charge-coupled device (CCD) technology to detect the unique patterns on the surface of your fingertip including ridges, marks, and valleys. By using an array of light-sensitive diodes and an analog-to-digital converter, a CCD camera takes a picture of your fingerprint which illuminates ridges with darker areas, and the valleys between ridges with lighter areas.
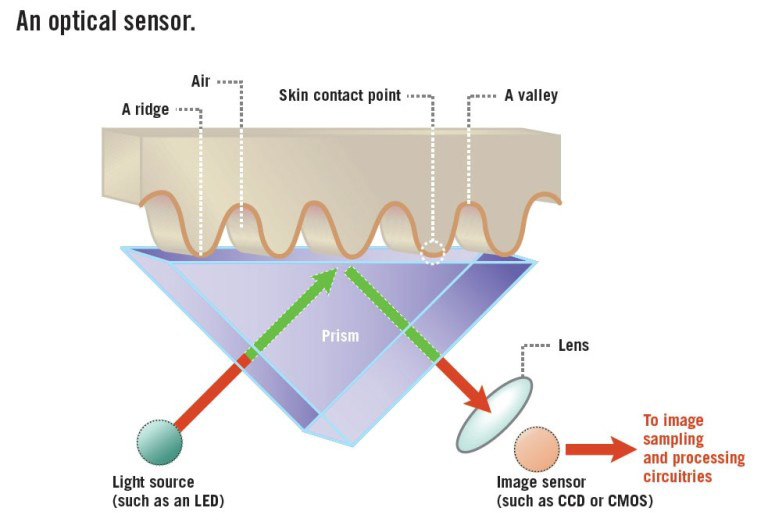
An optical sensor at work, using CCD cameras to sample the ridges and valleys in your fingerprint. (Image source)
Before this image of your fingerprint is stored, the processor in a CCD camera will first check for the average pixel darkness. If the overall image is too dark or light, then it gets rejected, and another image has to be taken. Once darkness levels are verified, the processor will then check the sharpness of the image by comparing several horizontal and vertical lines on your fingerprint. If all looks good, the fingertip is then accepted as a verified copy and can be stored for future comparisons.
As can be guessed, this method is easily susceptible to manipulation through the use of like-minded images or prosthetics of your fingerprint. Because of this flaw, optical scanners are now mostly obsolete and have been replaced by capacitive scanners.
Capacitive Scanners
Rather than relying on arrays of diodes in an optical scanner, capacitive scanners instead opt for an array of tiny capacitor circuits to analyze your fingerprint. By linking a bunch of capacitors to a conductive plate, any charges that occur by placing your finger on this plate will result in a change of charge in the capacitors.
For example, when the ridge of your fingerprint makes contact with the conductive plate, all surrounding capacitor charges are altered. At the same time, all of the valleys in your fingerprint with open air gaps will leave the capacitor’s charge unchanged. All of this data gets captured by an op-amp integrated circuit, which can then convert those physical analog signals into digital data through the help of an analog-to-digital converter.
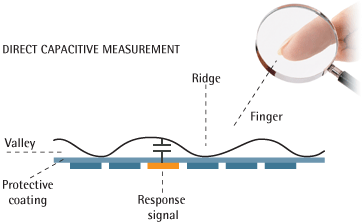
A capacitive scanner using capacitors and a contact plate to send the unique ridges and valleys in your fingerprint. (Image source)
Just like optical scanning, capacitive scanners will also analyze the captured image to look for unique characteristics in your fingerprint. However, capacitive scanners are much tougher to fool with prosthetics or other materials that might be used to mock a fingerprint since every material reacts differently to the conductive plate in the scanner.
As a big bonus for smartphone manufacturers, the chips in a capacitive scanner are also a whole lot more compact than a CCD camera system in an optical scanner. This makes them a perfect fit for the ultra-thin smartphones that we’re used to seeing these days.
Ultrasonic Scanners
The latest fingerprint scanning technology to enter the market is the ultrasonic sensor, being developed by Qualcomm with its Sense ID technology. The hardware in this scanner includes both an ultrasonic transmitter and receiver. How does it work? First, an ultrasonic pulse is transmitted to your fingertip, which gets absorbed or repelled depending on if it hits a ride of value in your fingertip. The signal that gets bounced back to the receiver is then able to map out the unique topology of your fingerprint in 3D! Check out the video below from Qualcomm to see how this technology works.
https://www.youtube.com/watch?v=FtKKZyYbZtw&feature=youtu.be
Keeping Your Fingerprints Secure
Regardless of what technology is being used to capture your fingerprint, all of the information being collected is stored within an ARM processor within your smartphone. This processor keeps your fingerprint data away from anyone that could intercept it, either from third party apps of your phone’s operating system. Having all of this information stored on a physical chip in a Trusted Execution Environment (TEE) is what allows your smartphone to communicate with other biometric hardware through a secure API without allowing any unintended intrusion.
The advantages of biometrics are pretty clear – rather than having to use something manual like a password or pin to access your information or applications, you can use the unique physical characteristics of yourself. That means no more having to remember passwords, or losing keys, or needing to carry around a device to verify your identity. You just use yourself! But this level of personalization with authentication and security raises some valid concerns, including:
There’s clearly a lot of issues that need to be worked out in biometric technology to make it accepted worldwide. But that hasn’t stopped us from already taking advantage of some great uses for it.
We focused pretty heavily in this blog on fingerprint scanning and how it has impacted consumer smartphones, but there are a ton more applications out there currently in use for biometric technology. Here’s just a few that showed up in 2016:
Banking
More and more banks have started to use biometric authentication in 2016 to create secure payment transactions and audit trails. In 2016 Citibank announced their plans for biometric authentication, and Visa has started to implement mobile biometrics.
Security
If you’ve ever flown into Los Angeles Airport (LAX) lately, then you’ve likely had to run through the new passport check-in terminals. These systems take advantage of facial recognition and passport scanning technologies to keep tabs on everyone entering the country.

Prepare for a complete biometric experience when arriving at LAX from an international flight. (Image source)
Healthcare
We’re also starting to see the use of biometric technology to accurately identify patients and pull up their associated medical records in hospitals. Back in August 2016, the University Health Care System rolled out their RightPatient® biometric patient identification platform, which allowed them to streamline the patient registration process through biometric facial scanning.
Automotive
Biometrics are also being used in the automotive industry in the form of biometric vehicle access systems. Maybe one day we won’t even need our Bluetooth enabled keys, and we’ll be able to use our fingers or voice to unlock and turn on our vehicles!
Want to unlock your car door? With biometrics, it might be a keyless process. (Image source)
Biometrics are everywhere, and the more you look into all of the commonplace technologies that you rely on each and every day, the more you’ll see biometrics in action. You likely already use biometrics to log into your smartphone that keeps you connected to your world, and maybe even your laptop now. And when you go to the doctors, you’ll soon be using biometrics to pull up all of your patient records. Your kids might even be using biometrics in school to get through the lunch line quicker, no more lunch money! But can we tackle the growing challenges of security, privacy, and control over one’s biometric data and make this a universal technology? Only time will tell.
Ready to get started designing the latest Biometrics technologies? Subscribe to Autodesk EAGLE today.
By clicking subscribe, I agree to receive the Fusion newsletter and acknowledge the Autodesk Privacy Statement.
Success!
May we collect and use your data?
Learn more about the Third Party Services we use and our Privacy Statement.May we collect and use your data to tailor your experience?
Explore the benefits of a customized experience by managing your privacy settings for this site or visit our Privacy Statement to learn more about your options.